Finding the Vulnerability
After reading this article, I found that one of my SSH servers was vulnerable to Terrapin attacks. I downloaded a free scanner and then ran it against the SSH server in question by using the following command:
Terrapin_Scanner_Windows_amd64.exe -connect hostname.local
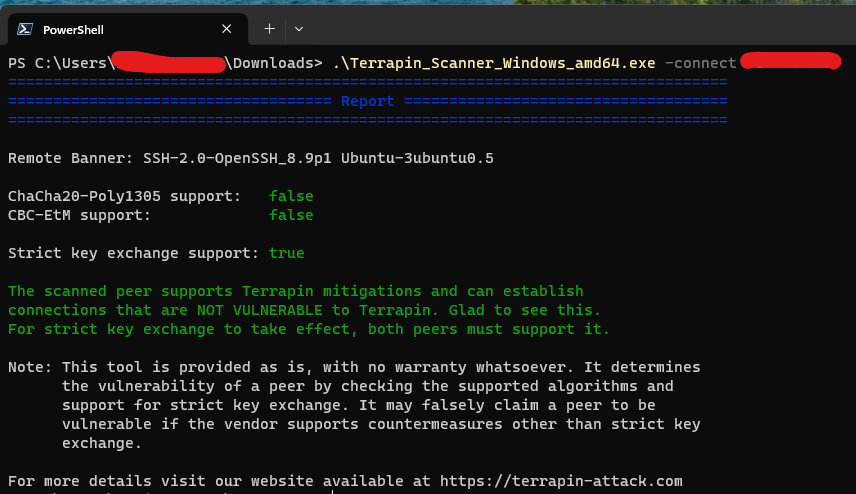
After which I received the following result:
This shows that the ChaCha20-Poly1305 cipher is enabled and is one of the vulnerable ciphers with Terrapin.
Fixing the Vulnerability
I modified my config file on the server which was found after reviewing the file:
/etc/ssh/sshd_config
I removed the ChaCha20-Poly1305 from the list of available ciphers and then restarted the SSH service by issuing the following command:
sudo /etc/init.d/ssh restart
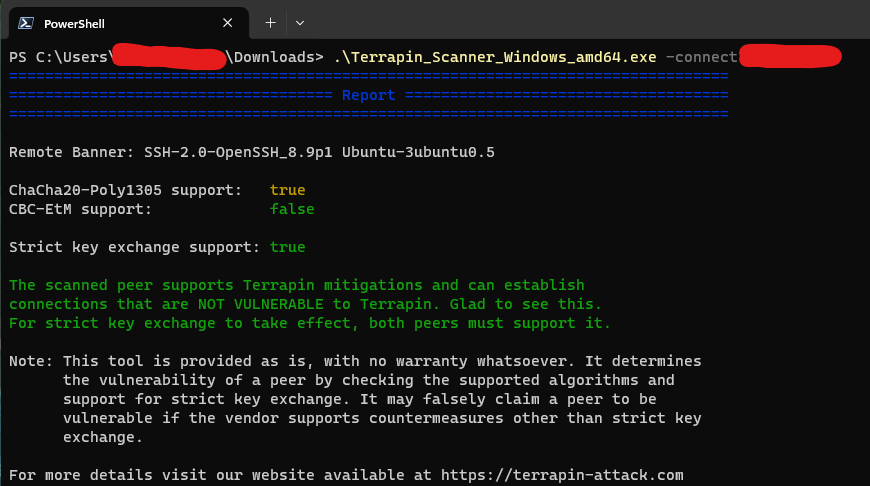
I then reran the Terrapin Scanner and was greeted with following screen showing that the vulnerability has been mitigated: