If you are currently administering a Binalyze server and would like to setup a trusted certificate using LetsEncrypt, then these instructions are for you.
Install Certbot
I am currently using Debian 12 for my Binalyze server. I was able to install Certbot using snap with the following command:
snap install certbot --classic
Run Certbot
We need to run this in manual mode since we will manually upload the certificates later. Additionally, Certbot will return a ECDSA format SSL certificate by default, but Binalyze needs an RSA type:
certbot certonly --manual --key-type rsa
- You will need to provide the domain name of the server. Example: air.example.com
- Certbot will ask you to upload a file to verify you own the domain you are creating a cert for. This was a bit tricky, but I was able to find out where to store the file by using the filename of one of the assets on the application. For example, the name of the background image was
sign-in-background-4a1729bd.webpfor my instance. I ran the following command to find out where on the filesystem this lives:
find / | grep sign-in-background-4a1729bd.webp
This gave me the following results:
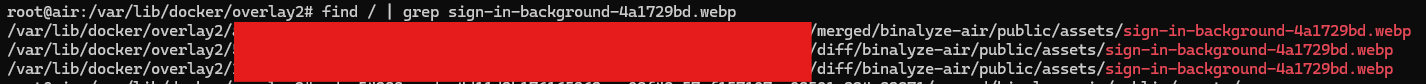
I assumed the merged folder was appropriate and determined that anything in the public folder would be served at the root which was correct. I created the file in the /var/lib/docker/overlay2/<redacted>/merged/binalyze-air/public/.well-known/acme-challenge folder, and Certbot was appeased with this and created the certificate files.
Upload the SSL Certificates to Binalyze
Within Binalyze, navigate to Settings > Security. Under SSL Certificate click on the Change button in the top-right hand corner
- For SSL Certificate, upload the
fullchain.pem. - For SSL Private Key, upload
privkey.pem. - Click Verify Settings
- Click Verify and Save
Binalyze will restart and you should now have a LetsEncrypt SSL cert installed!
Taking this further
LetsEncrypt certificates expire in 90 days, so we will need to regenerate the keys and reupload them before then. A couple of ideas:
- Maybe Certbot can be configured to do this within the docker container like a regular web server can. Something to play with.
- Maybe Binalyze can integrate this functionality in the product.
